Guard7 is a general purpose cryptography tool that used to encrypt or decrypt email, file, sign and verify files. It is the graphical frontend for the GNU Privacy Guard (GnuPG or GPG, http://www.gnupg.org) on macOS (previously Mac OS X) with additional features. Guard7 is an encryption and decryption system based on industry standard that can ensure the complete security of business negotiations or personal messages. It was developed to make the daily work with GnuPG on macOS easy and simple.
- Apple helps you keep your Mac secure with software updates. The best way to keep your Mac secure is to run the latest software. When new updates are available, macOS sends you a notification — or you can opt in to have updates installed automatically when your Mac is not in use. MacOS checks for new updates every day and starts applying them in the background, so it's easier and faster.
- WireGuard is a fast, modern, and secure VPN tunnel. This app allows users to manage and use WireGuard tunnels. The app can import new tunnels from archives and files, or you can create one from scratch. It is currently undergoing rapid development, and we are listening to our users in implementing new and exciting features.
- Explore the world of Mac. Check out MacBook Pro, MacBook Air, iMac, Mac mini, and more. Visit the Apple site to learn, buy, and get support.
- Garuda Linux is an appealing Arch Linux based Distro with BTRFS (modern filesystem), Linux-zen kernel, auto snapshots, gaming edition and a lot more bleeding-edge features.
Explore the world of Mac. Check out MacBook Pro, MacBook Air, iMac, Mac mini, and more. Visit the Apple site to learn, buy, and get support.
It's free!
If you can't open the link above, please launch App Store and found Guard7 by searching. Please kindly donate the author by purchasing other apps developed by the author or commend this app on your blog or rate this app so that helping other people can more easily find it.
Why
The most difference between 'public key cryptography' and normal 'password protected cryptography' is that the first approach don't ask you to distribute any password to anyone or any unsafe place, e.g. email, chat app, or internet. That is, you send an encrypted message or file to someone, but don't need send any password to him/her. And the most important point is, you need an encryption tool that has industrial strength to protect your confidential information.
General Features
- Group and subkey management.
- Drag operation for group organisation, easily manage hundreds of contacts by company and department.
- Seamlessly integrated with the built-in Mail app of macOS, easily organise dozens of recipients for email message.
- Encrypt, Decrypt email and file by conveniently dragging operation.
- Multiple keyring management. Switch between different keyring just requires a simple click.
- Import keyring and key from Linux, Mac, Windows and Unix, compatible with GnuPG 1.x and 2.x version and OpenPGP.
- Query, download or upload key to PGP key servers.
- Easily manage key and subkeys, edit key by simple click.
- Without complex installation, configuration or double boring questions.
Dangerous Operation
a. Don't import Keyring as public key.
b. Don't import key files that wasn't generated by Guard7.
(signature file, public key and private key)
The above two operation both are very dangerous.
They may crush your database and can't recover your data.
Basic Usage
You don't need to have deep knowledge of 'Public Key Cryptography' at all, you can get industry-level strength information protection with just a few simple steps.
- Generate a key pair for yourself.
Click and the system will generate a public and private key pair for you. You should send the public key to others who can then encrypt message for you. The private key is used to decrypt message and must be keeping for yourself. You SHOULD NOT send your private key to anybody, but keep it for yourself VERY CAREFULLY.
Note: This operation is very time-consuming, please wait a while with patient. - Distribute your public key.
Select your key, right click the node and then select 'Export Public Key', your public key file will be created. Put your public key in a GPG server, your web site or send it directly to others via chat app, email or other channel. - Import other people's public key.
Ask someone else to send his public key to you, or if he has already distributed his public key on GPG server, you need to download it and then simply drag the key file into the left side treeview to import it.
click the '+' symbol or click and then select the 'Import Public Key' menu or directly drag the key file into the left side treeview to complete the operation. - Use other people's public key to encrypt message, and then sent to them.
Drag their email (public key) into the right side drop-area as recipients, and then encrypt your message or file. - Decrypt message with your own private key.
If someone else has your public key, they can encrypt message with your public key, and then you can decrypt the message with your private key. When you decrypt a message or file, or verify file signature, you don't required to do any extra actions. The system will automatically use the default master key that you set to do the operation, i.e., you don't need to choose your own private key manually.
Encrypt or sign file follows the same steps and principles.
Group Contacts
Organise your contacts by company and department.
- Click to add new group.
- Click the minus symbol '-' under the tree to delete key or group.
- Add key to group: drag the primary key to the group that you want it belongs to.
- Delete association between key and group: drag the primary key out of the group to a blank space.
- Edit group name: click the group then edit its name just like in Finder.
Note: Drag operation only available for the primary keys that always display an email address.
File Types
- : .asc files, key file or signed signature file.
- : .gml files, encrypted email message.
- : .gpg files, encrypted and compressed File.
Name Rules
Public key has format: xx@xx_pubkey.asc.
Private key has format: xx@xx_privkey.asc.
Encrypt File
- Drag the file into the right side drop-area.
- Drag the recipients from left side treeview into the right side drop-area, repeat this operation to add more recipients.
- Click on the Toolbar.
- Select the output directory.
Note: It's not necessary to compress file before encrypt it, because Guard7 will compress it automatically.
Decrypt File
- Drag the file into drop-area.
- Click on the Toolbar.
- Select the output directory.
Encrypt and Decrypt Email
Sender
- Drag the recipients from the left side treeview into the right side drop-area.
- Click on the Toolbar to open mail box.
- Input your text in the mail box.
- Ensure the 'Attach to email' checked.
- Click 'Encrypt'
- The engine will launch the built-in Mail app of macOS and create a mail automatically.
- The content of the encrypted message will be attached in the mail with .gml extension name.
Tips: Use Up/Down arrow key to select multiple recipients.
Decrypt File
- Drag the file into drop-area.
- Click on the Toolbar.
- Select the output directory.
Encrypt and Decrypt Email
Sender
- Drag the recipients from the left side treeview into the right side drop-area.
- Click on the Toolbar to open mail box.
- Input your text in the mail box.
- Ensure the 'Attach to email' checked.
- Click 'Encrypt'
- The engine will launch the built-in Mail app of macOS and create a mail automatically.
- The content of the encrypted message will be attached in the mail with .gml extension name.
Tips: Use Up/Down arrow key to select multiple recipients.
Receiver
- Launch the macOS's built-in Mail app of macOS if it haven't opened.
- Select the mail that you want to view in Inbox.
- Click on the Toolbar to open mail box.
- Click 'Decrypt'
- Guard7 will decrypt the message attached in the selected email that has a .gml extension name.
View message file without open Mail App
- Save the attachment that has .gml extension to your disk.
- Click on the Toolbar if mail box haven't opened.
- Drag the .gml into mail box then the content will be decrypted automatically.
Encrypt and Decrypt Plain Text
Sender
- Drag the recipients from left side treeview into drop-area.
- Click on the Toolbar to open mail box.
- Input your text in the mail box.
- Uncheck the 'Attach to email'.
- Click 'Encrypt'.
- The engine will produce text with two marks, begin with '-----BEGIN PGP MESSAGE-----' and end with '-----END PGP MESSAGE-----'.
- Carefully copy the content and paste it into Web Mail (e.g. Gmail, Yahoo! Mail), Chat Apps (such as Jabber, ICQ, Skype, Viber, Google Hangouts, WhatsApp, LINE, Discord, Ventrilo, TeamSpeak, Kik, Slack, Telegram, etc), any software that you want to translate your confidential message.
Note: please ensure the begin and end mark included.
Receiver
- Click on the Toolbar to open mail box.
- Past text that has '-----BEGIN PGP MESSAGE-----' and '-----END PGP MESSAGE-----' marks.
- Uncheck the 'Attach to email'.
- Click 'Decrypt'.
- The engine will decode the message and output the result in the mail box.
With the help of Guard7 you can encrypt any text message and send it in any way convenient for you.
Sign File
- Drag the file into the right side drop-area.
- Drag your primary key from left side treeview into the right side drop-area.
- Click on the Toolbar.
- Select the output directory.
Verify File
- Drag the signature file into the right side drop-area.
- Click on the Toolbar.
- Select the location (directory) of the signed file, normally it should together with the signature file in the same directory.
Recipients Organisation
- Drag single key or several group form left side treeview into drop-area, single key means an individual and a group means all recipients in it.
- Right click to see more details of the selected key.
- Right click to remove some recipients.
Drag multiple groups into the drop-area enable you quickly organise dozens of recipients to receive your file or message. But if you use a command line software or other tools, you will have to organise the recipients one by one, it's very time waste and boring.
Operation with Finder
- Drag key file into the left side treeview then it will be imported.
- Drag encrypted file, signature file or message into the right side drop-area then you can decrypt, verify or read them.
- Select key file, signature file, encrypted file or message in Finder, right click 'Open With' then you can import key, verify, decrypt or read the message.
Keyring Management
keyring is a package working like a folder that binding group info, public and private key together, it's a common compressed zip file when you export a keyring. The system will automatically create a keyring named as 'home' for you if there's no any keyring exists when you run Guard7 at the first time.
Click 'Preferences' on main menu.
- Create new keyring.
When your contacts are too many, such as hundreds or even thousands, or other reasons you need to create a separate keyring for a large number of contacts. - Import or export keyring.
You need to import keyring from other system, e.g. Linux, and when backup or change hardware you need to export keyring. Please compress your ~/.gpg on Linux as a tar file when you want to import it into Guard7. - Switch keyring.
keyring enable you to organise group of contacts like folder and can conveniently switch between them.
Key Management
- Never send your private key to others.
- Keep your private key on a USB drive is a good method, but print it on paper and lock it in a safe will be more reliable.
- Backup your keyring carefully.
- Sign and encrypt messages with your subkey.
- Sign and encrypt files with your subkey.
- Verify a key in an efficient way is, directly make a phone call and ask he/she read out the fingerprint of his/her key.
subkey: the subnode under your primary key node (the node titled with your email address).
Edit Key (optional)
- Reset passphrase.
- Reset expire date.
- Set the key as your default master key.
- Create subkey separately used for encrypt or signing.
- Sign key with a different trust level. There's five trust level:
1 = Don't know
2 = I do NOT trust
3 = I trust marginally
4 = I trust fully
5 = I trust ultimately
This option help you to decide how far you trust this user to correctly verify other users' key and it is absolutely not necessary in daily usage.
Note: edit key is not necessary in daily usage scenario.
Simple Demonstration Session
The following steps emulate a session between two person on a same machine, here assume they're Tom and Mary, the steps can help you get an overview understanding of how 'Public Key Cryptography' works.
Step 1. Create key pair for Tom and Mary:
a. Click 'GenKeys' on toolbar to generate a key pair for Tom.
b. Select the created key and export Tom's public key and private key.
c. Click 'GenKeys' on toolbar to generate a key pair for Mary.
d. Select the created key and export Mary's public key and private key.
Please give the key pair an easily remember password for test only.
Now, you have four key files:
Tom@compnay_pubkey.asc
Tom@compnay_privkey.asc
Mary@compnay_pubkey.asc
Mary@compnay_privkey.asc
Step 2. Tom create an encrypted file with Mary's public key:
a. Right click Tom's public key and then select 'Edit Key', input password and on the prompt dialog select 'Primary', check on 'set as your primary key' and click 'Set as primary key' button.
b. Remove all key of Mary from the left side tree view.
c. Drag Mary@compnay_pubkey.asc into the left side tree view to emulate importing Mary's public key.
d. Drag the Mary's public key imported in the previous step from left side to the right side table as a Recipients.
e. Drag a sample file from Finder into the right side table and then click 'Encrypt' on the toolbar to encrypt it, a compressed file with '.gpg' extension name will be created.
Step 3. Mary decrypt the file with her own private key:
a. Remove all key from the left side tree view.
b. Drag Mary@compnay_pubkey.asc into the left side tree view to import Mary's public key.
c. Drag Mary@compnay_privkey.asc into the left side tree view to import Mary's private key.
d. Right click Mary's public key and then select 'Edit Key', input password and on the prompt dialog select 'Primary', check on 'set as your primary key' and click 'Set as primary key' button.
e. Drag the encrypted file that output from the step 2 and then click 'Decrypt' on the toolbar to decrypt it.
Guard7 on Apple App Store
This cryptography tool is one of the top best-sales security app on App Store from 2018, thousands of copy have been downloaded from that time and people across the planet use it to protect their confidential information everyday.
Note: One thing you must know is, they do very bad things on Apple App Store, these gentlemen leaves bad comments on the 'rate and comment' of some good apps or vice versa to mislead people, so please judge one app's value by yourself instead of what they said.
Guard7 on Wikipedia
There's a reference of Guard7 on wikipedia from Feb 2018, but some shameless 'gentleman' removed it viciously, again! again! and again! and again! Blocking edit again! again! and again! and again! They don't want this useful tool can be free used widely! Because they want control and make money!
After a long fight with them, they are not shameless 'gentleman' but bastard!
The reference have been removed by these guys, please kindly recover the content on that page to help others if you have permission. The page link is: https://en.wikipedia.org/wiki/GNU_Privacy_Guard, one of the 'gentleman': https://en.wikipedia.org/wiki/User:Zazpot. Please append the following block into the section Platforms on that page.
In 2018, Sevenuc Consulting released a free cryptograph utility named Guard7 on [[Mac App Store]] that make the daily work with GnuPG easy and simple on [[macOS]], it is a graphical frontend for GPG with some additional features, e.g. organise contacts into group, switch between different keyrings. Guard7 seamlessly integrated with the built-in Mail app of macOS to send and receive message conveniently, and can easily organise dozens of recipients for email message. Encrypt or decrypt file just require dragging the file from Finder into Guard7, it is very convenient and simple. {{cite web|url=http://www.sevenuc.com/en/guard.html|title=GUI frontend of GNU Privacy Guard on macOS}}
The more they maliciously attack this software, the more their bad intention are exposed, and the more affirmation of this software.
Feedback
Feature request and issue management on Github:
→ https://github.com/chengdu/Guard7, thanks.
Why Guard7 is free?
Mac OS X should has such a valuable and useful tool like Guard7 that can encrypt confidential information simple, easy and free.
Thanks
Here sincerely thanks the authors and contributors of GNU Privacy Guard, for your excellent works.
References
- GNU Privacy Guard, http://www.gnupg.org.
- Public key cryptography on Wikipedia, Public-key Cryptography.
About the developer
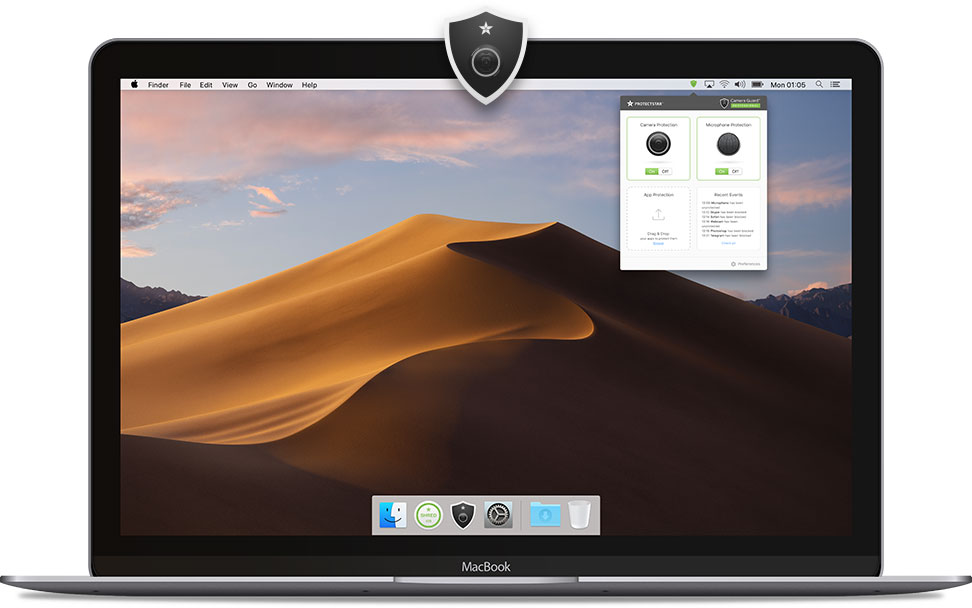
Protectstar is the leading company in the cybersecurity solution space. The cyber theft is increasing exponentially worldwide, and there is an ever-increasing threat to people's data. Protectstar has been instrumental in providing state of the art military trusted cybersecurity solutions to the customers. This ensures that people stay worry free when it comes to cybersecurity. So far, the developer has catered to the cybersecurity needs of over 4,000,000 users.
About the app
Camera Guard 3 Mac is a product that helps you safeguard your Mac device's camera and microphone module from any possible security breach. With one click, your camera and microphone become hack-proof.
Why you should download Camera Guard for mac
With hackers being on the rise, your data is never safe. Inevitable (jon oldblood) mac os. Even tech mogul like Mark Zuckerberg uses tape to cover the camera on his MacBook. Even if you take all the measures and do all the right things to protect yourself from the hacker attack, there is a lot of scope of hackers managing to get through all it is accessing the hardware on your device and stealing data.
With Camera Guard Mac, you can sit back relaxed that your Mac device's camera and microphone are locked and protected from hack attempts. Camera Guard has become a must-have application for all Mac users with tonnes of features and the best protection.
Features
1. Webcam and Microphone protection
With Camera Guard, not only your webcam but also the microphone on your device is safe from hacker attacks.
Mac Os Versions
2. App Locker
Along with webcam and microphone protection, the Camera Guard user also gets an additional app locker feature. This feature comes handy for those who share their Mac devices with their children or other people. This feature is useful to maintain the privacy of their content and allow access to whom you wish.
3. Deep Detective
In Camera Guard, the Deep Detective protection module permanently controls which process is currently accessing the encrypted data of your notes safe. It also reports known (and thanks to modern heuristic methods) it also reports unknown attacks.
With the Deep Detective, we have created an intelligent and versatile detective that observes all Android device accesses – similar to a firewall Detection System – only smarter. Deep Detective permanently controls which process or app currently attempts to access the camera. Additionally, it reports known – and thanks to modern heuristic methods – also unknown attack attempts. Every possibility to spy on you is proactively restricted from hackers, spies, and Trojans. With thousands of attack signatures, the optional Deep Detective Live spyware scanner offers comprehensive protection against many hacking attacks.
4. Smart ransomware protection
Using the latest technology, the smart Deep Detective™ is constantly monitoring and protecting critical system areas and your personal data with an additional layer of prevention against Mac encrypting ransomware attacks like KeRanger and more.
5. An Ideal combination
Camera Guard can, especially with activated Deep Detective, be used ideally in combination with other existing security solutions like anti-virus scanners or firewalls.
Anti-virus scanners and personal firewalls have already been stretched to their limits for years: With Camera Guard you surpass those limits, because the software observes and secures specific hardware components that couldn't be protected by modern security solutions – until now!
System Requirements
Supported Operating Systems for Software
- Mac OS 10.11 or higher (OS X El Capitan, macOS Sierra, macOS High Sierra, macOS Mojave, macOS Catalina)
Minimal Hardware Requirements
- Minimal system requirements of the operation system
- 50 MB free hard drive space
- Internet connection for updates and activation
- Compatible with all models of MacBook, MacBook Air, Macbook Pro, iMac, iMac Pro
Languages
- English, German
The Camera Guard Mac Professional editions comes with:
The Guard Mac Os 11
- Web camera protection
- Microphone protection
- Whitelist
- Protection against (un)known attack attempts
- Pop-Ups regarding security breaches
- Set a schedule for each app or all apps to allow unblocked usage for specific days and times.
- Supports Apple Touch ID on latest Macbook Pro.
- Deep Detective protection against known and unknown attack attempts incl. smart ransomware protection
- Securely protect Apps with a pin
- 24/7 Support by e-Mail

